
Add to Cart
Network Traffic Visibility Distribute Related Data from Network TAP
to Rlated Security Tools
What is Network TAP's Network Visibility?
Network visibility is enabling network administrators to capture,
replicate, aggregate, precess, forward, analysis and see network
traffic and applications that are traveling across Wide Area and
Local Area network links. Once captured, the network traffic can be
mapped to various tools for analytics, performance enhancement and
security. There are many specialized tools to perform these
functions that all must be connected to network links in order to
provide traffic data to tools. This connectivity is the foundation
of visibility and can be managed in one of three ways. Direct
connection is where the tools are connected directly to live links.
This allows the tool to directly see and manipulate traffic. It
becomes an integral part of the network and will be able to analyze
data, block data and send packets back into the network. The
primary limitation of direct in-line connection is potential
network disruption, if the tool should go off line due to a power
disruption, maintenance or any other reason make the network down.
If the tool goes down, the link goes down. If you have multiple
tools on a link, the probability for disruption increases
accordingly. There are also financial considerations with this
method. In target networks, it can be financially stressful to
deploy multiple network tools on every link.
Background Introduction
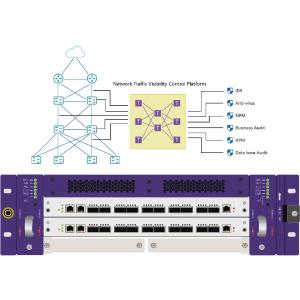
After 10 years of technology accumulation and precipitation, NetTAP
launched the Network Traffic Data Visibility Management and Control
Platform independently developed. It will realize your
comprehensive intelligent control over where network traffic data
assets come from and go.
This platform adopts the perfect combination of non-invasive SDN
Traffic Collection Distribution MATRIX and MATRIX Visual Control
System to present the existing network topology, acquisition
node, control platform and back-end application monitoring system
in a highly correlated manner, thus forming a unified global
Network Visibility monitoring management perspective.
Large-capacity Network Visibility 10G/40G/100G Capture, Aggregation
and Distribution Application, Distribute Related Data from Network TAP to Rlated Security Tools
Span deployment the high-performance, high-capacity MATRIX-TCA-CG
traffic acquisition visibility system to uniformly collect data
traffic of any node location and any link type (10G/40G/100G) on
the entire network, and then data traffic can be transmitted
through the system. The size, structure, relationship, etc. are
collated and analyzed. After the invisible data signal is converted
into a visible entity, the user can copy, aggregate, and offload
the required target data to each back-end system for depth
detection and analysis according to system requirements.
In this configuration, live network traffic passes through the TAP,
directly into the active tool and back into the network in real
time. This allows the tool to analyze the traffic, manipulate
packets, stop suspicious packets and take immediate action on the
link to block malicious traffic. These tools include Active
Firewall and Intrusion prevention systems (IPS/NGFW). The TAP in
the active stack has unique bypass technology that sends a
heartbeat to the active tool. If the tool goes off line for any
reason, the TAP can bypass the tool keeping live network traffic
flowing. When the heartbeat returns, traffic automatically returns
to normal operation flowing through the tool. Managing and
protecting network infrastructure and information requires focus.
Each of these devices specializes on a very tight functional range.
The example above is by no means a complete list of network
monitoring, management and security tool options. There are many
purpose built tools for applications such as Data Loss Protection
(DLP), Customer Experience Management (CEM), and Identity Access
Management (IAM). A simple web search will turn up a wide variety
of devices that can be added to these links based on specific
threats or required analysis. Having a multiple port TAP foundation
allows tools to easily and safely be added, repurposed or changed
depending on the immediate needs of the network. There is a logical
step by step flow when developing a visibility strategy; access,
capture, analyze, secure and remediate if necessary. Ideally, if
the right strategy and tools are in place along with other
organizational influences to be discussed later, the remediation
step will hopefully not be required. However, as is often said,
plan for the best but prepare for the worst.
Network Packet Broker Specification and Module Type
| Component type | Product Model | Basic Parameter | Remarks |
| Chassis | NTCA-CHS-7U7S-DC | Height:7U,7 slots, ATCA Chassis, double star 100G backplane, 3 high voltage DC(240VDC~280VDC) input,3* 2+1 redundant 3000W power modular | Must choose one |
| NTCA-CHS-7U7S-AC | Height:7U,7 slots, ATCA Chassis, double star 100G backplane, 3 high voltage AC(240VDC~280VDC) input,3* 2+1 redundant 3000W power modular | ||
| Service card | NT-TCA-SCG10 | 100G exchange card,10*QSFP28 interface | Choose according to actual business needs |
| NT-TCA-CG10 | 100G service card,10*QSFP28 interface | ||
| NT-TCA-XG24 | 10G service card,24*SFP+ interface | ||
| NT-TCA-RTM-CG10 | 100G RTM card,10*QSFP28 interface | ||
| NT-TCA-RTM-EXG24 | 10G RTM card,24*SFP+ interface | ||
| TCA Visibility Embedded software system | NT-TCA-SOFT-PKG | must |
Machine Specification
| Items | Specifications |
| Chassis size | NTCA-CHS-7U7S-DC:310.45mm(H) × 482.6mm(W)× 443.6mm(D) |
| NTCA-CHS-7U7S-AC:310.45mm(H) × 482.6mm(W)× 443.6mm(D) | |
| NTCA-CHS-16U14S-DC:708.35 mm(H) × 482.6mm(W)× 502.15mm(D) | |
| NTCA-CHS-16U14S-AC:708.35 mm(H) × 482.6mm(W)× 502.15mm(D) | |
| Adapter chassis and power | Power supply |
| NTCA-CHS-7U7S-DC:High voltage DC(240VDC~280VDC) | |
| NTCA-CHS-7U7S-AC:220V AC | |
| NTCA-CHS-16U14S-DC:High voltage DC(240VDC~280VDC) | |
| NTCA-CHS-16U14S-AC:220V AC | |
| Power: | |
| NTCA-CHS-7U7S-DC:Full configuration maximum power consumption < 3000W | |
| NTCA-CHS-7U7S-AC:Full configuration maximum power consumption < 3000W | |
| NTCA-CHS-16U14S-DC:Full configuration maximum power consumption < 5000W | |
| NTCA-CHS-16U14S-AC:Full configuration maximum power consumption < 5000W | |
| Environment requirement | Working temperature:0℃~50℃ |
| Storage temperature:-20℃~80℃ | |
| Working humidity:5%~95%,Non-condensation | |
| Standard Certification | Advanced®specification PICMG® 3.0 R2.0 |
| RoHs,Designed for CE,FCC,NEBS Level 3 |
